Comprehensive Network Traffic Analysis
Network traffic analysis demands specialized tools capable of intercepting
and decoding data streams fragmented into digital packets during transmission
Modern solutions address critical infrastructure challenges including
undiagnosed latency spikes, hidden security breaches, and unexplained bandwidth consumption
Key operational hurdles resolved by advanced packet analysis:
- Unidentified protocol errors causing application performance degradation
- Stealthy malicious activities bypassing conventional security measures
- Recurring cyber incidents from undetected compromised devices
- Operational blind spots in troubleshooting intermittent connectivity failures
Leading solutions diverge in analytical depth and deployment flexibility:
Real-time Traffic Processors
ManageEngine NetFlow Analyzer (multi-platform support) provides protocol-level insights
across hybrid environments with flow data interpretation capabilities
Paessler PRTG integrates multiple sensor types for comprehensive traffic forensics
Forensic Analysis Specialists
Omnipeek delivers granular protocol dissection for performance optimization
SolarWinds combines deep packet inspection with root-cause diagnostics
Lightweight Utilities
TShark offers Wireshark's core functionality in command-line format
Windump brings Unix-style packet capture to Windows environments
Fiddler specializes in web transaction monitoring through HTTP/S lens
Selection criteria prioritizes adaptive functionality:
- Traffic decryption capabilities for encrypted threat detection
- Customizable alert thresholds for anomaly identification
- Automated baseline establishment for deviation tracking
- Cross-platform compatibility with existing monitoring ecosystems
- Forensic timeline reconstruction for incident analysis
ROI assessment requires evaluating operational efficiency gains against:
- Reduced mean-time-to-detect security incidents
- Prevented compliance violations through traffic auditing
- Optimized resource allocation via bandwidth pattern analysis
- Labor cost savings from automated diagnostics
Implementation strategies vary by organizational scale:
Enterprise environments benefit from ManageEngine's tiered licensing model
(starting at $1,045 for advanced threat hunting capabilities)
Mid-sized operations might prioritize PRTG's sensor-based pricing structure
Technical teams should evaluate free tools like NetworkMiner
for foundational traffic pattern recognition training
Ultimate tool effectiveness hinges on correlating raw packet data
with contextual network behavior profiles across infrastructure layers
ManageEngine NetFlow Analyzer is a robust tool designed to gather and analyze traffic information from your network devices. It offers versatile options for traffic sampling, capturing entire streams, or collecting statistics on traffic patterns.
Key Features of ManageEngine NetFlow Analyzer:
- Traffic Shaping: This feature allows administrators to control and optimize data flow within the network, ensuring efficient use of bandwidth.
- Multi-Protocol Support: The tool supports a wide range of network flow protocols, including NetFlow, IPFIX, sFlow, J-Flow, NetStream, and AppFlow, making it compatible with various network devices.
- User-Friendly Interface: The interface is designed to be easy to navigate, even in high-volume networks, providing clear and usable insights for administrators.
- Protocol Analysis: It identifies traffic volumes per application, helping to pinpoint which applications are consuming the most bandwidth.
- VoIP Quality Measurements: The tool tracks Mean Opinion Score (MOS) and Class-Based Quality of Service (CBQoS) to ensure high-quality VoIP connections.
By combining flow-based traffic monitoring with deep packet inspection, ManageEngine NetFlow Analyzer provides detailed and granular insights into network performance and security. This real-time packet capture feature enables IT admins to thoroughly analyze server traffic and application behavior, converting raw data into actionable insights to identify and address performance bottlenecks and security threats.
ManageEngine stands out as one of the most stable companies in the industry, known for its extensive product suite and large employee base. The company's dedicated customer support team, coupled with high customer satisfaction and comprehensive self-documentation, contributes to its strong support system.
The NetFlow Analyzer primarily uses network device query languages such as NetFlow, sFlow, and J-Flow. These systems analyze packets and store statistics related to packet header values within the switch or router. When the analyzer queries this information, it retrieves data derived from packet inspection. To manage storage efficiently, the tool extracts statistics about packet headers rather than capturing entire packets, which can be very space-intensive due to the high volume of network traffic.
To accommodate different network devices, the NetFlow Analyzer is capable of using multiple communication protocols, including Cisco NetFlow, Juniper Networks J-Flow, and Huawei NetStream, as well as sFlow, IPFIX, and AppFlow standards. This versatility ensures that the tool can gather and analyze data from a wide array of network equipment.
The tool also monitors the consistency of data flows and the load on each network device. It allows you to see and capture packets as they pass through a device, enabling you to identify which applications are using the most bandwidth. This visibility helps in making informed decisions about traffic shaping measures, such as priority queuing or throttling.
The dashboard features color-coded graphics, making it easier to spot and address network issues. The visually appealing and user-friendly console is built on a common platform, allowing seamless integration with other ManageEngine infrastructure monitoring tools. For instance, many network administrators opt to use both OpManager and NetFlow Analyzer from ManageEngine to streamline their network management.
ManageEngine NetFlow Analyzer offers comprehensive network monitoring capabilities with its dual focus on device status tracking and traffic pattern analysis. This powerful tool is compatible with multiple operating systems including Windows, Windows Server, and various Linux distributions such as RHEL, CentOS, Fedora, Debian, SUSE, and Ubuntu.
The software comes in two distinct editions to meet different organizational needs. The Essential Edition provides standard traffic monitoring functionality plus reporting and billing features. For more advanced requirements, the Enterprise Edition builds upon these core capabilities by adding NBAR & CBQOS monitoring, enhanced security analytics, capacity planning tools, and deep packet inspection. Additional features in this premium tier include IP SLA and WLC monitoring.
Network administrators seeking to optimize hardware performance and implement effective traffic shaping will find significant value in NetFlow Analyzer. The system helps prioritize time-sensitive traffic without requiring additional capacity investments. While a free version exists, its limitation to only two interfaces makes it impractical for most scenarios.
The software can be deployed to monitor either a single network or a WAN environment. Installation options include Windows Server, Linux, or cloud deployment through AWS.
During evaluation, several strengths were identified including pre-configured templates for quick insight extraction, cross-platform compatibility, and enterprise-focused features like SLA tracking. The tool also offers packet capture capabilities for stress testing and flexible cloud hosting options. However, its enterprise-centric design makes it less suitable for small networks or home users with basic requirements.
Both editions are available with a 30-day free trial period. NetFlow Analyzer stands out for providing real-time visibility into network traffic, applications, and devices, enabling effective monitoring and analysis of traffic patterns.
The solution supports multiple flow technologies including NetFlow, sFlow, J-Flow, and IPFIX, making it adaptable to diverse network environments. Its user-friendly interface features graphics-rich dashboards and customizable reports that simplify troubleshooting and anomaly detection.
Additional advanced capabilities include traffic shaping, capacity planning, and forensic analysis tools. The software integrates seamlessly with other ManageEngine products, particularly the OPManager network device monitoring solution.
Pricing is aspect-based, with each aspect representing one metric per device. The minimum package starts at 500 aspects for $179 monthly.
PRTG Network Monitor: A Comprehensive Packet Sniffing Solution
PRTG Network Monitor stands out in the crowded field of network monitoring tools by offering an integrated approach to infrastructure management. This all-in-one solution combines robust packet sniffing capabilities with comprehensive network monitoring features.
Core Functionality
PRTG functions as both a network performance monitor and bandwidth analyzer, giving administrators complete visibility into their network infrastructure. The dual approach allows users to simultaneously monitor device status and analyze traffic patterns across network links.
Packet Capture Capabilities
The packet capture component of PRTG focuses on header information rather than full packet content. This strategic design choice offers two significant advantages:
- Enhanced processing speed
- Reduced storage requirements
Traffic Visualization and Analysis
The system organizes captured traffic into intuitive categories including:
- Email communications
- Web browsing activities
- Chat application data
- File transfer operations
This categorization enables administrators to quickly identify traffic patterns and potential bottlenecks.
Multiple Protocol Support
PRTG's versatility extends to its compatibility with various flow protocols:
- NetFlow
- sFlow
- J-Flow
This multi-protocol support ensures the tool can integrate with virtually any network environment regardless of the devices deployed.
Real-Time Monitoring Features
Administrators benefit from several real-time monitoring capabilities:
- Live traffic visualization
- Customizable alert thresholds
- Performance troubleshooting tools
- Abnormal activity detection
Integration Benefits
What truly distinguishes PRTG is its seamless integration with other monitoring methodologies:
- SNMP polling
- WMI queries
- Flow protocol analysis
This integrated approach provides deeper insights than standalone packet sniffers can deliver.
Organizational Considerations
While PRTG offers excellent documentation and support resources, potential users should note that Paessler's relatively small team size may occasionally impact support responsiveness. However, the company's strong financial position suggests continued product development and improvement.
Value Proposition
PRTG's sensor-based licensing model delivers exceptional value, allowing organizations to activate only the monitoring components they need. This flexibility makes it suitable for networks of various sizes and complexities.
NetFlow technology remains a cornerstone in network traffic monitoring across multiple vendors. Originally developed by Cisco Systems, this data flow messaging protocol has expanded beyond its proprietary origins to become an industry standard utilized by numerous hardware manufacturers.
The PRTG monitoring suite includes robust NetFlow sensor capabilities that extend to IPFIX (IP Flow Information Export) - the IETF-standardized evolution of the original NetFlow protocol. This compatibility ensures broader coverage across modern network infrastructures.
Juniper Networks implements a parallel system called J-Flow for their networking equipment, functioning similarly to NetFlow by continuously monitoring packet streams. This continuous capture methodology differs significantly from sFlow, which employs a sampling approach that only examines periodic packets (every nth packet) rather than the complete traffic flow.
Both NetFlow and J-Flow provide comprehensive traffic analysis through uninterrupted packet stream monitoring, while sFlow trades complete coverage for reduced processing overhead through its sampling technique.
Exploring PRTG's Flexible Sensor-Based Network Monitoring Solution
PRTG Network Monitor offers a unique approach to network monitoring through its sensor-based pricing model. Each network condition or component you monitor counts as one sensor, including the four available packet sniffing interfaces. This structure makes PRTG particularly accessible for smaller organizations, as implementations using 100 sensors or fewer are completely free of charge.
The scalability of PRTG is one of its standout features. Organizations can start small and expand their monitoring capabilities as needed by activating additional sensors. This flexibility extends to deployment options as well, with both on-premises Windows Server installations and cloud-based SaaS solutions available.
For network administrators focused on packet analysis, PRTG provides efficient header-only capture capabilities. This approach significantly reduces storage requirements while still delivering the essential data needed for troubleshooting and analysis. The system presents this information through straightforward but effective visualization tools that make interpretation intuitive.
While PRTG offers comprehensive monitoring beyond just packet sniffing—including virtualization and application monitoring—new users should be prepared for an initial learning curve. The depth of features available means some time investment is required to fully leverage the platform's capabilities.
PRTG's pricing for larger implementations starts at $2,967 annually for a single user license, making it particularly suitable for medium to large enterprise environments requiring high-speed packet analysis. Organizations interested in exploring the platform can take advantage of a 30-day free trial before committing to a purchase.
Omnipeek, which was previously offered by Savvius, is a comprehensive network protocol analyzer designed to capture and analyze network traffic. It provides in-depth protocol analysis, making it an invaluable tool for troubleshooting and optimizing network performance.
Key Features of Omnipeek:
- Protocol Analysis : Omnipeek serves as a robust protocol analyzer, helping users interpret and understand network protocols. This feature is essential for diagnosing and enhancing network performance.
- Packet Capture : The tool includes packet capture capabilities, allowing users to examine and monitor network traffic in real-time or for historical analysis. This is crucial for both diagnostic and monitoring purposes.
- Wireless Network Support : Omnipeek extends its functionality to wireless networks, making it a versatile solution for both wired and wireless environments.
Omnipeek offers real-time and historical packet analysis, combined with deep packet inspection, providing detailed insights into network traffic. Its intuitive visualizations and expert analysis help in quickly identifying and resolving network and security issues. The tool supports a wide array of protocols, making it well-suited for complex network environments.
With Omnipeek, you can gain instant visibility into network traffic across various segments, including high-speed internet and wireless networks. It can decode thousands of protocols in real-time, providing immediate information about network events.
The protocol analyzer in Omnipeek samples passing packets on a specific network device, compiling statistics on traffic sources, destinations, and protocols. You can also set it to capture packets for further viewing. By default, Omnipeek focuses on packet headers for analysis, but it can also sample traffic on wireless networks. The system can be configured to analyze all network traffic or just the traffic intended for a specific device interface, allowing for targeted link examination.
Omnipeek's functionality can be extended through plug-ins. The core Omnipeek system does not natively capture network packets, but adding the Capture Engine plug-in enables this capability. The Capture Engine captures packets on wired networks, while the WiFi Adapter extension adds wireless capabilities, allowing for the capture of WiFi packets through Omnipeek.
In addition to protocol analysis, Omnipeek monitors network performance. It lists traffic by protocol and measures transfer speed and regularity, raising alerts if traffic slows down or exceeds predefined boundary conditions set by the network administrator.
The traffic analyzer can track end-to-end transfer performance across the entire network or focus on individual links. It also monitors interfaces, such as incoming traffic to web servers from external sources. The software emphasizes traffic throughput, displaying data as lists of protocols and their throughput or as live graphs and charts. Packets captured with the Capture Engine can be stored for analysis or replayed across the network for capacity testing.
Windows-compatible network diagnostics tool with subscription-based licensing
Enables real-time bandwidth consumption analysis across devices/users
Customizable performance alerts for throughput anomalies detection
Forensic packet inspection with traffic simulation capabilities
Key advantages include low system resource consumption during operation
Historical data replay function assists in predicting infrastructure needs
Limitations involve dated visual layout affecting workflow efficiency
Trial version available for pre-purchase functionality verification
Optimal for complex environments requiring application dependency mapping
Targets corporate networks blending cloud and physical infrastructure
Contact sales for enterprise-tier pricing structures
SolarWinds Deep Packet Inspection Tool: A Comprehensive Network Analysis Solution
Network administrators face numerous challenges when monitoring and troubleshooting complex environments. Among the powerful solutions available today is the Deep Packet Inspection and Analysis Tool from SolarWinds, which offers sophisticated capabilities for network traffic analysis.
This powerful tool serves as an integral component of the SolarWinds Network Performance Monitor (NPM) ecosystem, enabling administrators to decode and analyze over 1,200 different applications. By examining network traffic at the packet level, it provides critical insights that help distinguish between network-related and application-related performance issues.
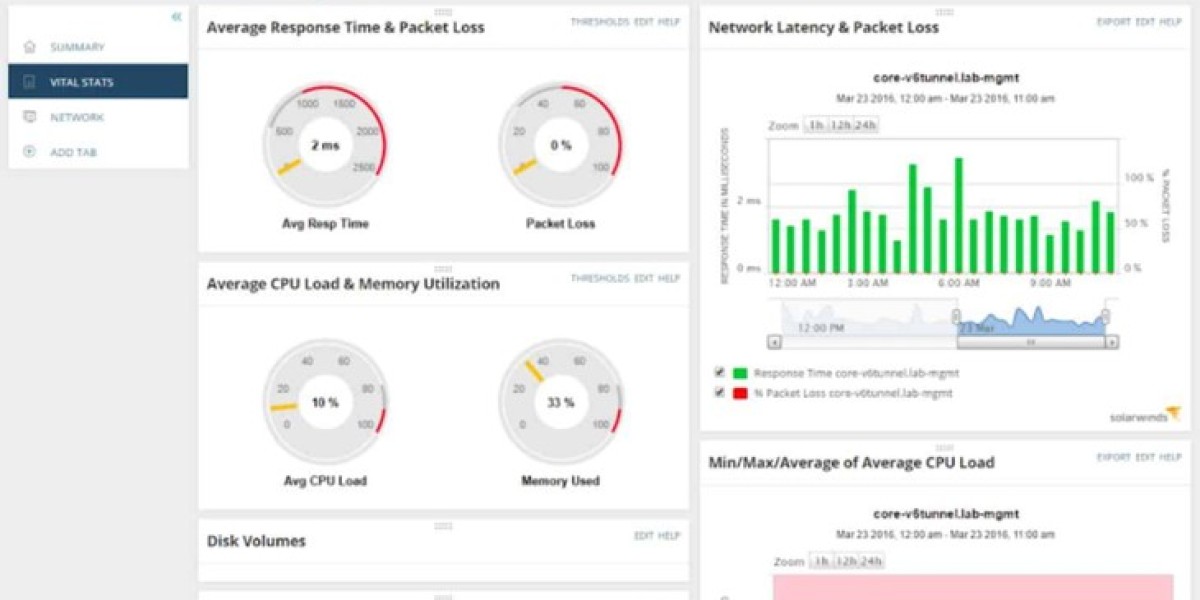
One of the standout features is the Quality of Experience (QoE) dashboard, which presents real-time information about network latency, server response times, and overall application health. This immediate visibility allows IT teams to make data-driven decisions quickly when troubleshooting performance problems.
The tool excels at categorizing network traffic, giving administrators clear visibility into the types of data flowing through their infrastructure. Its protocol stack analyzer capabilities enable detailed examination of communication layers, while real-time monitoring ensures no critical events go unnoticed. Additionally, the traffic shaping support helps optimize data flow across the network.
For organizations managing hybrid environments, this solution offers enhanced performance monitoring across both physical infrastructure and cloud deployments. While the tool cannot decrypt encrypted packet contents (maintaining data confidentiality), it effectively analyzes unencrypted headers to gather valuable information about protocols and endpoints.
This deep inspection capability addresses common challenges that basic analysis tools struggle with, such as identifying which specific applications are generating traffic, determining where users are spending their time online, and pinpointing connections that may be causing network slowdowns.
SolarWinds offers a 30-day free trial of this tool, allowing potential users to evaluate its capabilities before committing to a purchase. The company itself has built a solid reputation with comprehensive self-help documentation and dedicated customer support, though some have noted employee satisfaction issues.
For network professionals seeking deeper insights than simple traffic flow data, the SolarWinds Deep Packet Inspection and Analysis Tool represents a valuable addition to their troubleshooting arsenal.
Network traffic analysis demands a blend of technical precision and contextual awareness.
While tools like NetFlow and sFlow form the backbone of monitoring strategies, their effectiveness hinges on how they’re deployed—each protocol caters to specific infrastructure needs, balancing granularity with scalability.
Yet, mastery goes beyond tool selection. Interpreting data patterns requires not just protocol literacy but also familiarity with a network’s unique architecture and traffic norms.
Even the most detailed flow records remain cryptic without the intuition to spot irregularities, a skill forged through hands-on troubleshooting and deep system understanding.
In this field, theoretical knowledge and real-world exposure are inseparable allies.
The Network Monitoring Landscape: Tools for Packet Analysis
Network monitoring has become essential for maintaining optimal system performance and security. Whether you're managing enterprise infrastructure or troubleshooting connectivity issues, having the right packet sniffing tools can make all the difference.
For enterprise environments, comprehensive solutions like SolarWinds Network Performance Monitor offer robust capabilities. This professional-grade tool excels in environments where detailed network visibility is crucial. While it requires a Windows Server environment and comes with a price tag that may deter smaller organizations, its value becomes apparent in complex networking scenarios.
The standout features of enterprise monitoring solutions typically include:
- Automated discovery and inventory management
- Deep packet inspection capabilities
- Support for industry-standard flow protocols
- Visual alerting systems that highlight potential issues
- Centralized monitoring across distributed networks
For those operating in Unix/Linux environments, TCPdump remains the gold standard for lightweight packet analysis. As a command-line utility that comes pre-installed on most Unix-like systems, TCPdump offers tremendous power with minimal resource requirements.
TCPdump's enduring popularity stems from several key attributes:
- Zero cost barrier to entry
- Minimal system resource requirements
- Powerful filtering language for targeted captures
- Ability to write captures to files for later analysis
- Compatibility with other analysis tools in the ecosystem
When using TCPdump, it's essential to implement filtering at collection time. Without proper filters, even moderately busy networks can generate overwhelming amounts of data. The tool's expression-based filtering system allows precise targeting of specific protocols, ports, or traffic patterns.
A practical example demonstrates TCPdump's investigative value. During routine monitoring, unexpected traffic to an unfamiliar IP address (172.217.11.142) was detected. Further investigation revealed this was Google Chrome running as a background service, despite no browser windows being open. This kind of discovery highlights how packet analysis can reveal subtle system behaviors that might otherwise go unnoticed.
For most networking professionals, the ideal approach combines lightweight capture tools like TCPdump with more sophisticated analysis platforms. This hybrid methodology allows for efficient data collection in resource-constrained environments while enabling detailed examination when necessary.
Packet Capture Tools Overview
Exploring Command-Line Packet Capture Tools: A Deep Dive into tcpdump and Alternatives
Command-line packet sniffers remain essential tools for network administrators, offering lightweight solutions for traffic analysis without requiring resource-intensive graphical interfaces. Among these tools, tcpdump stands out as a veteran option beloved by system administrators working on headless servers.
tcpdump's command-line nature makes it particularly valuable in production environments where graphical interfaces would consume unnecessary resources. While its syntax requires a learning curve with its complex filtering language, the tool's efficiency compensates for this initial challenge.
The primary limitation of tcpdump is platform restriction—it's designed for Unix-like systems and isn't natively available for Windows. However, captured packets are stored in the industry-standard pcap format, allowing for analysis in various specialized tools.
Basic usage is straightforward, with commands like:
tcpdump -i eth0 -w captured_packets
This captures traffic from the eth0 interface and saves it to a file for later analysis. The resulting file requires specialized software for viewing, as it's not stored in plain text format.
For Windows administrators seeking similar functionality, WindDump provides a comparable solution. This tcpdump port brings the same capabilities to Windows systems through the WinPCap library. WindDump maintains the same command structure and capabilities while adapting to Windows networking architecture.
A key advantage of WindDump is its portability—once WinPCap is installed on a system, the WindDump executable can run without installation, making it convenient for technicians working across multiple systems. This allows administrators to carry the tool on portable media and deploy it as needed.
Both tcpdump and WindDump excel at packet capture but have limitations when it comes to analysis. For more comprehensive examination, Wireshark offers a superior solution. This free, open-source tool combines capture capabilities with powerful analysis features, including:
- Intuitive color-coding of different packet types
- Real-time traffic monitoring
- Conversation tracking to follow complete network exchanges
- Advanced filtering options for isolating specific traffic patterns
Wireshark's widespread adoption has created a substantial community, ensuring abundant documentation and support resources. Its availability across virtually all operating systems makes it a universal standard for network analysis.
For administrators considering which tool best fits their needs, tcpdump and WindDump are ideal for lightweight capture tasks, particularly on resource-constrained systems. Meanwhile, Wireshark provides the most comprehensive solution for environments where detailed analysis is required alongside capture capabilities.Analyzing Server Traffic: Remote vs. Desktop Approaches
When monitoring network activity on servers, your approach depends on the server's configuration. For servers with desktop environments installed, comprehensive packet analysis can be performed directly on the machine.
However, most production servers run headless configurations without graphical interfaces. In these common scenarios, the preferred method involves capturing packet data remotely, saving it as a pcap file, and transferring it to your analysis workstation.
When launching your analysis software for the first time, you'll typically have two options: begin a new capture session or open a previously saved pcap file for examination. During capture initialization, you can implement filters to narrow down the collected data.
One advantage of using robust analysis tools is that precision filtering during initial capture becomes less critical. The comprehensive examination capabilities allow you to collect broader datasets and apply detailed filtering during the analysis phase instead. If you choose not to specify any filters, your network interface will capture all observable traffic, providing a complete picture of network activity.
Wireshark's stream analysis feature reveals full communication contexts
with a simple right-click maneuver. When sifting through captured data floods,
focusing on specific interactions becomes effortless by selecting
a target IP (like the example's suspected Google server) and activating
the TCP stream tracker. This functionality reconstructs entire protocol dialogs,
transforming packet dumps into readable exchanges between devices.
Network troubleshooters gain critical visibility into application-layer chatter,
whether analyzing web requests, API calls, or unexpected traffic patterns.
To examine previously captured network data,
launch Wireshark and navigate to File > Open
to load saved .pcap files.
All analysis features—including filtering protocols,
statistical tools, and traffic visualization—
function identically for imported files
as they do for live network captures.
This flexibility allows retrospective investigation
of network activity with the same precision
as real-time monitoring.
A staple in networking courses, Wireshark often serves as the gateway tool for aspiring analysts.
Its open-source nature and plugin ecosystem make it adaptable, though mastery demands deep protocol knowledge.
The tool’s default "capture-everything" approach can overwhelm novices, requiring meticulous filtering skills.
For headless environments, Tshark emerges as Wireshark’s CLI counterpart, ideal for scripted workflows.
Leveraging the same filtering syntax, it enables automated packet processing without GUI dependencies.
Example use cases include cron-based monitoring or parsing traffic via commands like:
tshark -i eth0 -y http.request -t fields -e ip.dst
While Tshark excels in scripting, it lacks Wireshark’s visual analysis strengths.
Both tools share steep learning curves, particularly for those unfamiliar with BPF syntax.
Tshark’s lightweight design proves advantageous for server-side diagnostics, whereas Wireshark dominates interactive troubleshooting.
Key differentiators:
- Deployment Flexibility : Tshark integrates with CI/CD pipelines; Wireshark suits real-time desktop analysis
- Data Handling : Tshark’s stream processing minimizes storage needs vs Wireshark’s detailed packet storage
- Community Resources : Wireshark boasts extensive forums; Tshark users often rely on man pages and CLI docs
Despite their complexity, both tools remain free—a critical factor for educational institutions and budget-conscious teams.
Advanced users frequently combine them, using Tshark for capture and Wireshark for deep inspection.In the realm of enterprise cybersecurity, forensic analysis tools serve as critical components for incident response teams. Among these specialized solutions, NetworkMiner stands out as a distinctive option that transcends traditional packet sniffing functionality.
Unlike conventional network monitoring tools, NetworkMiner operates primarily as a network forensics analyzer, focusing on evidence collection and detailed traffic investigation rather than simple packet capture. This nuanced approach makes it particularly valuable for security professionals who need to reconstruct digital evidence from network communications.
One of NetworkMiner's most powerful capabilities is its ability to reconstruct files transmitted across networks. While standard packet sniffers might allow you to view individual packets or follow TCP streams, NetworkMiner takes this further by reassembling complete files from captured network traffic - an invaluable feature during security investigations.
The tool offers a free edition with core functionality, making it accessible for smaller teams or initial evaluations. For organizations requiring advanced features and comprehensive support, the Professional edition is available at $1,300, positioning it as an investment for serious enterprise security operations.
Security teams in large corporate environments particularly benefit from NetworkMiner's forensic-focused approach, as it provides the detailed evidence collection capabilities essential for thorough incident response and potential legal proceedings following security breaches.
NetworkMiner: A Comprehensive Network Traffic Analysis Tool
NetworkMiner stands out as a powerful passive network forensics tool that offers both packet sniffing and analysis capabilities. When strategically positioned within a network, it can silently observe traffic without generating any of its own data packets, making it ideal for discreet monitoring operations.
Unlike more complex alternatives, NetworkMiner presents captured information through an intuitive visual interface, eliminating the need to memorize complex filtering commands. This accessibility makes it particularly appealing to analysts who prefer straightforward approaches to network investigation.
One of NetworkMiner's standout capabilities is its ability to reconstruct various elements from captured packets. The tool excels at extracting files, images, and user credentials, while also rebuilding TCP streams to provide comprehensive views of network communications. These reconstructed elements prove invaluable when identifying the root causes of network issues.
The tool offers flexible deployment options. While primarily designed for Windows environments, NetworkMiner can run on Linux and macOS systems through the Mono framework. Additionally, it supports offline analysis by importing PCAP files captured using other tools like tcpdump, making it adaptable to various operational scenarios.
NetworkMiner comes in both free and premium versions. The free version delivers essential functionality for basic network analysis, while the Professional edition unlocks advanced features including GeoIP location services and custom scripting capabilities.
For organizations struggling with Wireshark's complexity, NetworkMiner presents a viable alternative with its more approachable query language. However, users should be aware of its somewhat dated interface, which might initially seem less intuitive compared to more modern analysis tools.
NetworkMiner is particularly recommended for web developers, security teams, and network administrators who need to analyze HTTP traffic and conduct forensic investigations without disrupting live network operations.
When developing web applications, understanding real-time data exchange between clients and servers is crucial.
Fiddler emerges as a specialized solution for intercepting and modifying HTTP/HTTPS traffic without delving into raw packet analysis.
Unlike traditional network sniffers that require reassembling fragmented packet data, it operates at the application layer for instant readability.
This proxy-based tool shines in scenarios where developers need to inspect headers, cookies, and API payloads in transit.
Its traffic interception capabilities extend to decrypting HTTPS streams, offering visibility into encrypted communications.
Users can manipulate live sessions by altering response codes or injecting errors to test application resilience.
A standout feature is the ability to simulate latency and bandwidth constraints, enabling performance testing under varied network conditions.
The interface presents captured sessions with color-coded entries, mirroring diagnostic approaches found in lower-level analyzers but tailored for web protocols.
This visual categorization helps quickly identify error states, redirects, and successful transactions.
For troubleshooting, developers can replay modified requests or create automated traffic sequences through scripting integrations.
The platform's focus on web-specific diagnostics makes it particularly valuable for validating REST API interactions and single-page application behaviors.
By exposing hidden data exchanges, it becomes easier to optimize payload sizes and identify redundant network calls during development cycles.
Fiddler, a versatile tool for web application developers and IT operations teams, is particularly beneficial in DevOps environments. It is available in both free and paid versions, making it accessible for a wide range of users. While it natively runs on Windows, it can also be used on Linux and macOS through the Mono framework, adding to its flexibility.
During our evaluation, we identified several advantages and disadvantages of Fiddler:
- Specialized HTTP Traffic Capture : Fiddler excels at capturing HTTP traffic, offering a more focused and less complicated solution compared to broader network analysis tools.
- Security and Communication Analysis : This tool is especially useful for those needing to analyze the security and communication aspects of HTTP protocols, providing in-depth insights into web traffic.
- Free Version Availability : Fiddler is completely free to use, which means users can access its features without any cost, making it an attractive option for budget-conscious individuals and organizations.
- Steep Learning Curve : One of the main drawbacks is its steep learning curve, particularly for users who are new to web debugging and proxy tools. This can make the initial setup and usage challenging.
- Limited Support Options : Users may find it difficult to get support for specific issues, as Fiddler does not have as extensive a support community as some other tools, which can be a drawback for those needing quick assistance.
Best Use Case:
- Real-time packet capture
Relevant For:
- Managed Service Providers (MSPs) in enterprise environments
Pricing:
- Free
- Standard: $295
- Enterprise: $995
Exploring Capsa Network Analyzer: A Comprehensive Packet Analysis Tool
Capsa Network Analyzer stands out in the packet sniffing landscape with its tiered approach to network analysis. The entry-level Capsa Free version offers essential packet capture capabilities with a visually intuitive analytical interface. This version serves as an excellent starting point for networking enthusiasts looking to develop their packet analysis skills.
The graphical dashboard sets Capsa apart from competitors, making complex network data accessible even to those with limited packet analysis experience. For novice system administrators, this visual approach can significantly reduce the learning curve when troubleshooting network issues.
Despite being a free offering, this version delivers impressive functionality with support for over 300 protocols. Users can monitor email traffic, save email content for further analysis, and implement trigger-based alerts for specific network conditions. These capabilities extend the tool's utility beyond simple packet capture into a practical support tool.
Advanced features include the transformation of captured data into graphical representations, providing enhanced visualization of network communication patterns. The live traffic monitoring capabilities allow administrators to identify abnormal patterns and diagnose latency issues in real-time.
A key advantage of Capsa is its GUI-driven interface, eliminating the need for specialized programming knowledge. This accessibility doesn't come at the expense of functionality – users can still apply traffic filters and customize display screens to focus on relevant data.
The application layer inspection capabilities enable deeper analysis of performance and security issues, making Capsa valuable for both troubleshooting and security monitoring purposes. This dual functionality consolidates multiple networking tools into a single, comprehensive environment.
For junior system administrators and networking professionals, Capsa offers an accessible entry point into the world of packet analysis while providing the depth of features required for serious network monitoring and troubleshooting.
Capsa, a protocol analyzer, is compatible with Windows 2008, Vista, 7, 8, and 10. It is particularly suitable for small businesses in need of a free network monitoring solution. For those requiring more advanced features, there are paid editions available.
One of the key advantages of Capa is its user-friendly interface, making it an ideal choice for junior system administrators. It supports over 300 protocols even in its free version, providing a comprehensive set of features without the need for a subscription.
However, Capa is not as lightweight as command-line interface (CLI) tools, which might be a drawback for users seeking more resource-efficient options. Additionally, professionals may find its interface bulky and less efficient compared to more streamlined, minimalist CLI-based solutions.
For larger networks, where on-demand monitoring becomes impractical, enterprise-level tools like SolarWinds, with its 30-day free trial, can help manage and simplify the vast amount of network data.
To build an on-demand network monitoring infrastructure, you could install packet sniffing tools like tcpdump or windump on all servers. A scheduler, such as cron or Windows Task Scheduler, can be used to initiate packet collection sessions at specific times and save the data to pcap files. Later, a sysadmin can transfer these packets to a central machine and use Wireshark for analysis.
Packet sniffers offer several benefits, including:
- Identifying congested links
- Pinpointing applications that generate the most traffic
- Collecting data for predictive analysis
- Highlighting peaks and troughs in network demand
The actions taken based on this information depend on the available budget. If resources allow, expanding network capacity can be targeted more effectively. Otherwise, traffic shaping measures such as prioritizing application traffic, resizing subnets, rescheduling heavy-traffic events, limiting bandwidth for specific applications, or replacing inefficient applications can be implemented.
Understanding how your computer's network interface controller (NIC) operates is crucial when using packet sniffing software. By default, the NIC only captures traffic addressed to its MAC address. To capture all network traffic, the NIC must be set to "promiscuous mode." Most packet sniffers include a utility to manage this mode switch.
Effective network traffic analysis requires a solid understanding of networking fundamentals, such as the TCP three-way handshake, ARP, and DHCP traffic. This knowledge is essential for interpreting the data collected by packet sniffing tools. Without it, it can be challenging to identify and address network issues accurately.
For enterprise-level networks, more advanced tools are necessary. While many tools are built on tcpdump, enterprise solutions offer additional features like correlating traffic from multiple servers, intelligent query tools, alerts for exceptions, and generating detailed reports. These tools focus on network traffic flow rather than packet content, helping to maintain network performance and predict potential bottlenecks.
It's important to note that packet sniffers can also be used maliciously. They can be employed for wiretapping, man-in-the-middle attacks, and data theft. Therefore, investing in intrusion detection systems is crucial to protect your network from unauthorized access and potential threats.
Packet sniffers play a crucial role in network management by duplicating and analyzing data as it traverses the network. When deployed on a switch, these devices can be configured to send copied packets to a secondary port, effectively duplicating traffic. The captured data is often saved to a file, and some advanced tools even display this information in a user-friendly dashboard. However, packet sniffers can amass a vast amount of data, including sensitive administrative details, necessitating the use of specialized analysis tools to interpret and contextualize the information.
A basic packet sniffer captures all packets, which can lead to storage issues if you are monitoring network usage over extended periods. To mitigate this, sampling techniques, such as capturing every 10th or 20th packet, can be employed. This approach reduces the volume of data without significantly impacting the quality of the analysis.
Our methodology for selecting packet sniffers involves a detailed evaluation of each tool's features, their suitability for various environments, and real-world user feedback. We also conduct hands-on testing to assess the user interface and overall functionality. Our structured evaluation process focuses on several key aspects:
Technical Features:
We prioritize tools with robust technical capabilities, such as the ability to capture and decode packets across multiple protocols, including TCP, UDP, HTTP, DNS, and more. Additional points are awarded for tools that support real-time packet capture, filtering, and analysis.
System Performance:
While technical prowess is essential, we also consider the tool's impact on system performance. Ideal solutions should have minimal resource usage and be compatible with a wide range of platforms. Tools that maintain high performance while using limited resources are ranked higher.
Use Cases:
Flexibility is a critical factor. We favor tools that can be applied across different industries and use cases, and those that can scale to monitor large volumes of traffic.
Usability:
An intuitive interface is crucial for user adoption. Tools with out-of-the-box reporting templates and easy-to-navigate interfaces are given preference.
Support and Documentation:
Vendor support and comprehensive documentation are also important. We evaluate the availability of dedicated support teams, self-help resources, and community support.
These criteria align with our broader B2B methodology, which combines technical features with usability and support to provide a holistic view of each platform. Integration with existing tech stacks is also an implicit factor in our analysis.
In addition, we have developed a proprietary scoring system called SupportScore. This evaluates various factors, such as employee count, dedicated customer support, historical success, job satisfaction, financial stability, and the quality of self-supporting documents. The resulting score, ranging from 0 to 10, helps businesses make informed decisions about vendor support.
Transparency and honesty are fundamental to our business. We provide honest reviews and are transparent about our processes, including how we earn commissions.
PCAP, or "packet capture," refers to tools that copy and store network packets. These tools can either capture entire packets, including their data payload, or just the headers. Full packet capture creates large files, typically stored with a .pcap extension. While this method provides comprehensive data, it can raise confidentiality concerns, especially if the data is not encrypted.
Our research indicates that top-tier network traffic analysis tools include SolarWinds Deep Packet Inspection and Analysis Tool, Paessler Packet Capture Tool, ManageEngine NetFlow Analyzer, and OmniPeek Network Protocol Analyzer. Popular open-source options like tcpdump, windump, and Wireshark are also widely used.
Packet analyzers, which can be implemented as standalone devices or software, need to offer utilities for viewing, searching, and filtering packet data. Some analyzers include advanced analysis features.
Detecting packet sniffing can be challenging but is possible under certain conditions. For instance, a software-based packet sniffer requires the host computer’s network adapter to be in promiscuous mode. By pinging each computer on the network with the correct IP address but incorrect MAC address, you can identify hosts in promiscuous mode, indicating potential packet sniffing activity.
Full packet capture, which includes the data payload, is typically stored in .pcap files. However, due to the potential for data breaches, many organizations restrict the use of full packet capture to ensure compliance with data security standards.
What is a Netflix VPN and How to Get One
A Netflix VPN is a service that enables users to unlock geographically restricted streaming content by connecting to servers in different regions. It works by masking the viewer’s IP address, granting access to Netflix libraries exclusive to specific countries, such as shows or movies unavailable locally. Many users rely on a Netflix VPN to broaden their entertainment choices or maintain privacy while streaming.
Why Choose SafeShell as Your Netflix VPN?
If you’re struggling with a Netflix vpn not working due to geo-blocks or buffering, SafeShell VPN offers a reliable solution to unlock global content effortlessly. Unlike outdated VPNs that fail to bypass Netflix’s detection systems, SafeShell combines high-speed servers optimized for streaming with advanced obfuscation technology, ensuring seamless access to region-restricted libraries. Whether you’re binge-watching in HD or exploring international shows, its lightning-fast connections eliminate lag and throttling, transforming your viewing experience into a smooth, buffer-free journey.
SafeShell VPN prioritizes versatility and security, allowing you to connect up to five devices simultaneously across platforms like iOS, Android, smart TVs, and more. Its exclusive App Mode lets you switch between regional Netflix libraries without disconnecting, while the proprietary ShellGuard protocol encrypts your data, shielding it from ISP tracking or cyber threa